The Smart Office Security Challenge
As we move through 2025, the modern workplace has transformed dramatically. What started as simple Wi-Fi networks and desktop computers has evolved into complex ecosystems of connected devices managing everything from lighting and climate control to security systems and collaboration tools. Your office likely contains dozens of IoT devices that most employees—and even IT staff—barely think about from a security perspective.
 This proliferation of smart office technology creates unprecedented security challenges that traditional IT security approaches simply weren’t designed to handle. Unlike personal computers with standardized security software, IoT devices often ship with minimal security features, rarely receive updates, and frequently communicate using protocols that bypass traditional network security monitoring.
This proliferation of smart office technology creates unprecedented security challenges that traditional IT security approaches simply weren’t designed to handle. Unlike personal computers with standardized security software, IoT devices often ship with minimal security features, rarely receive updates, and frequently communicate using protocols that bypass traditional network security monitoring.
Why Standard IT Security Falls Short in Smart Offices
The IoT Security Gap
Traditional enterprise security focuses on protecting servers, workstations, and network infrastructure. But smart office devices operate differently:
- Minimal built-in security: Most IoT devices prioritize functionality and cost over security
- Infrequent updates: Many smart devices never receive security patches after deployment
- Non-standard communication: IoT protocols often bypass traditional network security tools
- Shadow IT proliferation: Departments deploy smart devices without IT oversight
- Vendor diversity: Each device type comes from different manufacturers with varying security standards
Business Risk Amplification
Smart office security failures can impact your business in ways that go far beyond traditional IT breaches:
- Operational disruption: Compromised building systems can affect productivity and safety
- Compliance violations: Many industries have regulations covering IoT device security
- Intellectual property theft: Smart meeting room systems and collaboration tools contain sensitive business information
- Physical security compromise: Connected access control and surveillance systems create new attack vectors
- Reputation damage: Security incidents involving workplace systems can affect customer and employee confidence
The Hidden Risks in Your Connected Workplace
Smart Meeting and Collaboration Systems
Modern conference rooms contain sophisticated technology that creates unique security challenges:
- Smart displays and videoconferencing systems that may record or transmit sensitive meetings
- Room booking systems that reveal organizational structure and meeting patterns
- Interactive whiteboards that store and potentially transmit brainstorming sessions
- Voice-activated assistants that may inadvertently capture confidential discussions
Building Infrastructure and Controls
Connected building systems offer convenience and efficiency but also create new vulnerabilities:
- Smart HVAC systems that can be compromised to affect workplace comfort and productivity
- Connected lighting systems that may reveal occupancy patterns and work schedules
- Occupancy sensors that track employee movement and space utilization
- Smart access control that could be manipulated to grant unauthorized building access
Office Equipment and Productivity Tools
Even basic office equipment has become “smart” and network-connected:
- Smart printers and multifunction devices that store document history and network credentials
- Digital signage systems that could be compromised to display malicious content
- Asset tracking systems that monitor equipment location and usage patterns
- Smart emergency systems critical for workplace safety and regulatory compliance
The Value of DIY Smart Office Security Assessment
Immediate Visibility Without IT Overhead
Professional cybersecurity assessments for smart office environments can take weeks to schedule and require significant IT resources. Our DIY assessment provides immediate insights into your current security posture without disrupting daily operations or requiring external consultants.
Cost-Effective Risk Identification
Before investing in expensive security solutions or professional services, understanding your actual risk profile helps prioritize security investments. The assessment identifies the most critical vulnerabilities first, enabling strategic security planning rather than reactive purchases.
Compliance Preparation
Many industries now have regulations covering IoT device security in workplace environments. Our assessment helps identify compliance gaps and provides specific recommendations aligned with international standards like NIST CSF, ISO 27001, and industry-specific requirements.
Ongoing Security Monitoring
Smart office environments evolve constantly as departments add new devices and update existing systems. Regular DIY assessments enable continuous security monitoring without the cost and complexity of ongoing professional services.
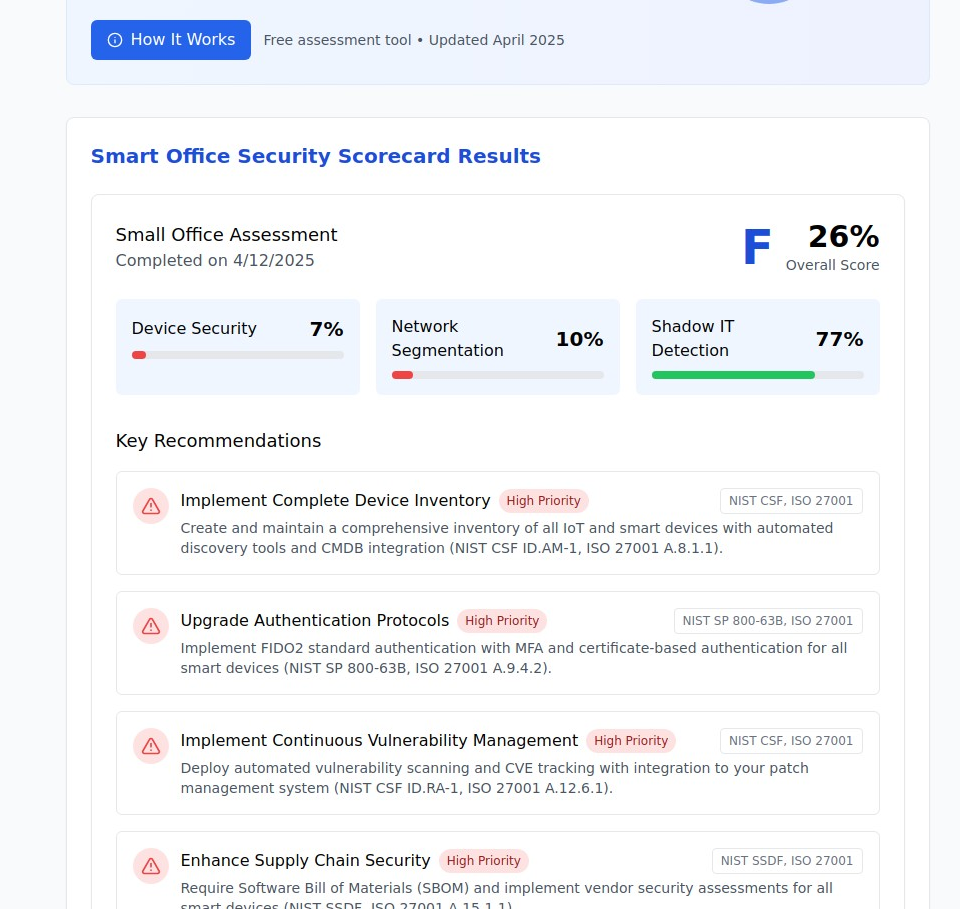
Comprehensive Smart Office Security Evaluation
Device Discovery and Classification
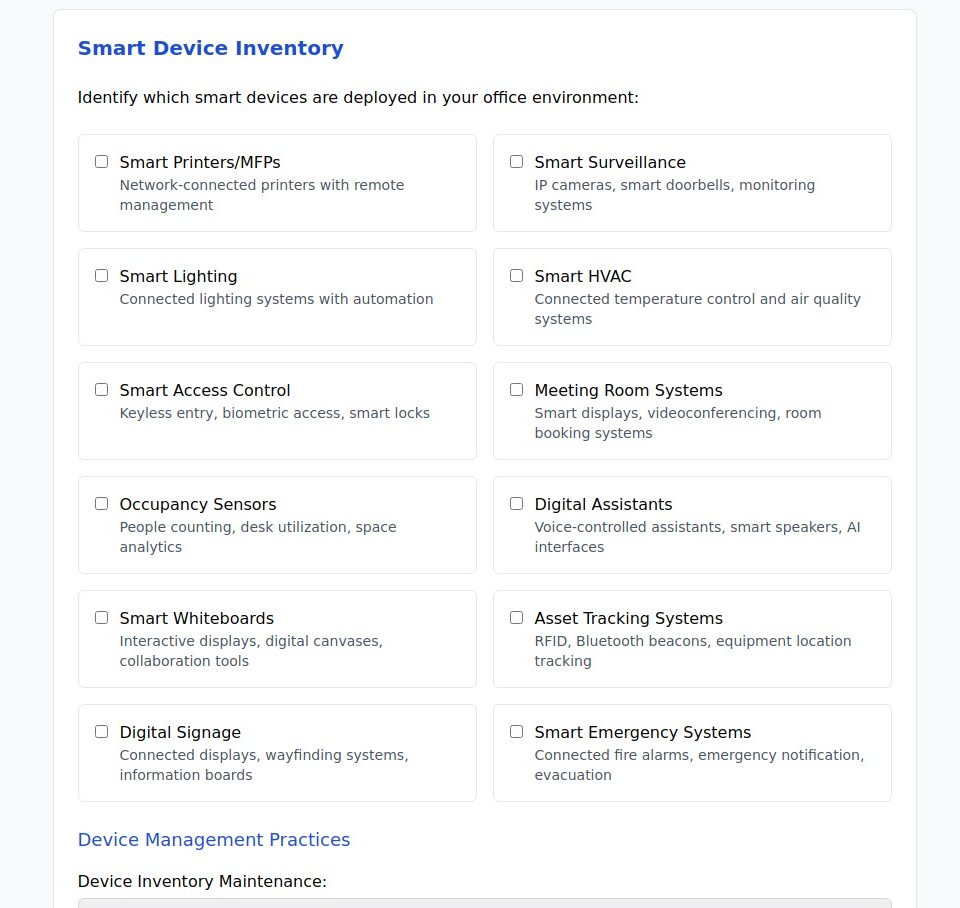
Complete inventory management: The assessment begins with identifying all connected devices in your workplace environment, including:
- Visible systems: Printers, displays, cameras, and access control systems that employees interact with daily
- Infrastructure devices: HVAC controls, lighting systems, and building management equipment that operate behind the scenes
- Collaboration tools: Meeting room technology, digital assistants, and communication systems
- Security equipment: Surveillance cameras, alarm systems, and monitoring devices
- Shadow IT devices: Unauthorized smart devices that departments may have deployed independently
Risk categorization: Each device category receives specific security analysis based on:
- Data access and storage capabilities
- Network communication patterns
- Update and patch management status
- Default security configurations
- Integration with critical business systems
Network Architecture and Segmentation
IoT network isolation: Effective smart office security requires sophisticated network design:
- Device segmentation isolating IoT devices from business-critical networks
- Access control limiting which devices can communicate with each other
- Traffic monitoring identifying unusual device behavior or communication patterns
- Guest network separation protecting business systems from visitor devices
Advanced threat detection: Modern smart offices need monitoring capabilities that extend beyond traditional IT security:
- IoT-specific monitoring designed for device communication patterns
- Behavioral analysis identifying devices that deviate from normal operation
- Automated response isolating potentially compromised devices
- Incident correlation linking smart office security events with broader cybersecurity threats
Shadow IT and Unauthorized Device Detection
Comprehensive device discovery: Many smart office security issues stem from devices deployed without IT oversight:
- Unauthorized device identification finding smart devices that bypass standard procurement
- Department-level deployments identifying devices purchased by individual teams
- Personal device integration managing employee smart devices that connect to business networks
- Vendor-installed equipment discovering devices installed by service providers or contractors
Governance and policy development: Effective smart office security requires clear policies:
- Device approval processes ensuring all smart devices meet security standards
- Vendor security requirements establishing minimum security criteria for new purchases
- Employee awareness training helping staff understand smart office security implications
- Regular audit procedures maintaining ongoing visibility into device deployments
Compliance and Standards Alignment
International framework compliance: Smart office security must align with established cybersecurity frameworks:
- NIST Cybersecurity Framework guidance for smart office risk management
- ISO 27001 controls specific to IoT device security in workplace environments
- Industry-specific requirements tailored to healthcare, finance, government, and other regulated sectors
- Supply chain security ensuring vendor compliance with relevant security standards
Implementation: From Assessment to Secure Smart Office
Quick Wins and Immediate Improvements
Most smart office assessments reveal several security improvements that can be implemented immediately:
- Default credential changes on all connected devices
- Firmware updates bringing devices to current security levels
- Network segmentation isolating smart devices from business systems
- Access control review ensuring only authorized personnel can manage smart office systems
- Monitoring system deployment providing visibility into IoT device behavior
Strategic Security Planning
Comprehensive smart office security typically requires longer-term planning:
- Architecture redesign implementing proper network segmentation and monitoring
- Policy development creating governance frameworks for smart device deployments
- Staff training programs building security awareness across all departments
- Vendor management establishing security requirements for future smart office purchases
- Incident response planning preparing for smart office-specific security events
Professional Service Integration
While DIY assessment provides valuable initial insights, many organizations benefit from professional services for:
- Penetration testing specifically targeting IoT devices and smart office systems
- Ongoing monitoring providing 24/7 surveillance of smart office environments
- Compliance consulting ensuring adherence to industry-specific IoT security requirements
- Architecture consulting designing comprehensive smart office security frameworks
- Incident response expert assistance during smart office security events
Privacy and Confidentiality in Assessment
Secure Local Processing
Smart office security information reveals detailed insights about your business operations, technology infrastructure, and potential vulnerabilities. Our assessment tool processes all information locally in your browser—no sensitive data is transmitted to external servers or stored in cloud systems.
No External Dependencies
Complete your comprehensive smart office security evaluation without creating accounts, connecting to external services, or sharing information with third parties. Your business security information remains completely under your control throughout the assessment process.
Actionable Results Without Exposure
Receive detailed, prioritized recommendations and security scoring without exposing your office infrastructure information to outside parties. You control whether and how to share assessment results with security vendors or professional services.
Tailored Assessment for Different Office Sizes
Small Office (1-50 employees)
Smaller offices often have the most diverse smart device deployments with the least formal oversight:
- Resource-constrained security focusing on high-impact, low-cost improvements
- Simplified compliance addressing essential requirements without extensive overhead
- Employee education ensuring all staff understand their role in smart office security
- Vendor consolidation reducing complexity through standardized smart device procurement
Medium Office (51-250 employees)
Mid-size organizations typically have more formal IT processes but still struggle with IoT security:
- Departmental coordination managing smart device deployments across multiple teams
- Policy development creating scalable governance frameworks
- Professional service evaluation determining when to engage external security expertise
- Compliance program development preparing for regulatory requirements and audits
The Business Case for Smart Office Security
Risk Mitigation
Smart office security failures can result in consequences that extend far beyond typical IT incidents:
- Business disruption when building systems are compromised or malfunction
- Compliance penalties for failing to secure IoT devices in regulated industries
- Intellectual property theft through compromised collaboration and meeting systems
- Physical security breaches when connected access control systems are manipulated
- Reputation damage affecting customer confidence and employee trust
Competitive Advantage
Organizations with mature smart office security demonstrate:
- Operational reliability through well-secured building and collaboration systems
- Compliance readiness for customers and partners with strict security requirements
- Innovation capability safely adopting new workplace technologies
- Employee confidence in workplace privacy and security measures
Getting Started with Smart Office Security
Your smart office security assessment provides the foundation for protecting your connected workplace. In just 10-15 minutes, you’ll receive a comprehensive evaluation of your current security posture across all critical areas, along with prioritized recommendations for improvement.
The assessment covers device security, network segmentation, shadow IT detection, and provides specific guidance aligned with international cybersecurity frameworks. All processing happens locally in your browser, ensuring your business information remains completely private.
Ready to secure your smart office environment?
Start Your Private Assessment →
Smart Office Security Scorecard | IoT Device Risk AssessmentEvaluate your smart office security posture with our comprehensive IoT device risk assessment tool.Secure IoT Office
 Your assessment is completely confidential—all processing happens locally in your browser. No business data is stored, transmitted, or shared. You’ll receive immediate, actionable insights to enhance your smart office security posture.
Your assessment is completely confidential—all processing happens locally in your browser. No business data is stored, transmitted, or shared. You’ll receive immediate, actionable insights to enhance your smart office security posture.
Why Smart Office Security Can’t Wait
As IoT devices continue proliferating in workplace environments, the security risks will only increase. Organizations that proactively assess and secure their smart office infrastructure will be better positioned to:
- Prevent costly security incidents that disrupt business operations
- Meet evolving compliance requirements for IoT device security
- Safely adopt new workplace technologies that enhance productivity
- Maintain employee and customer confidence in organizational security capabilities
The question isn’t whether your smart office needs better security—it’s whether you’ll address vulnerabilities proactively or reactively. Take control of your smart office security today.






